Kubernetes NodePort 端口封禁 - iptables Drop
Kubernetes NodePort是比较危险的操作,整个集群中每个Node都会创建一个端口,增加了整个集群的被攻击面
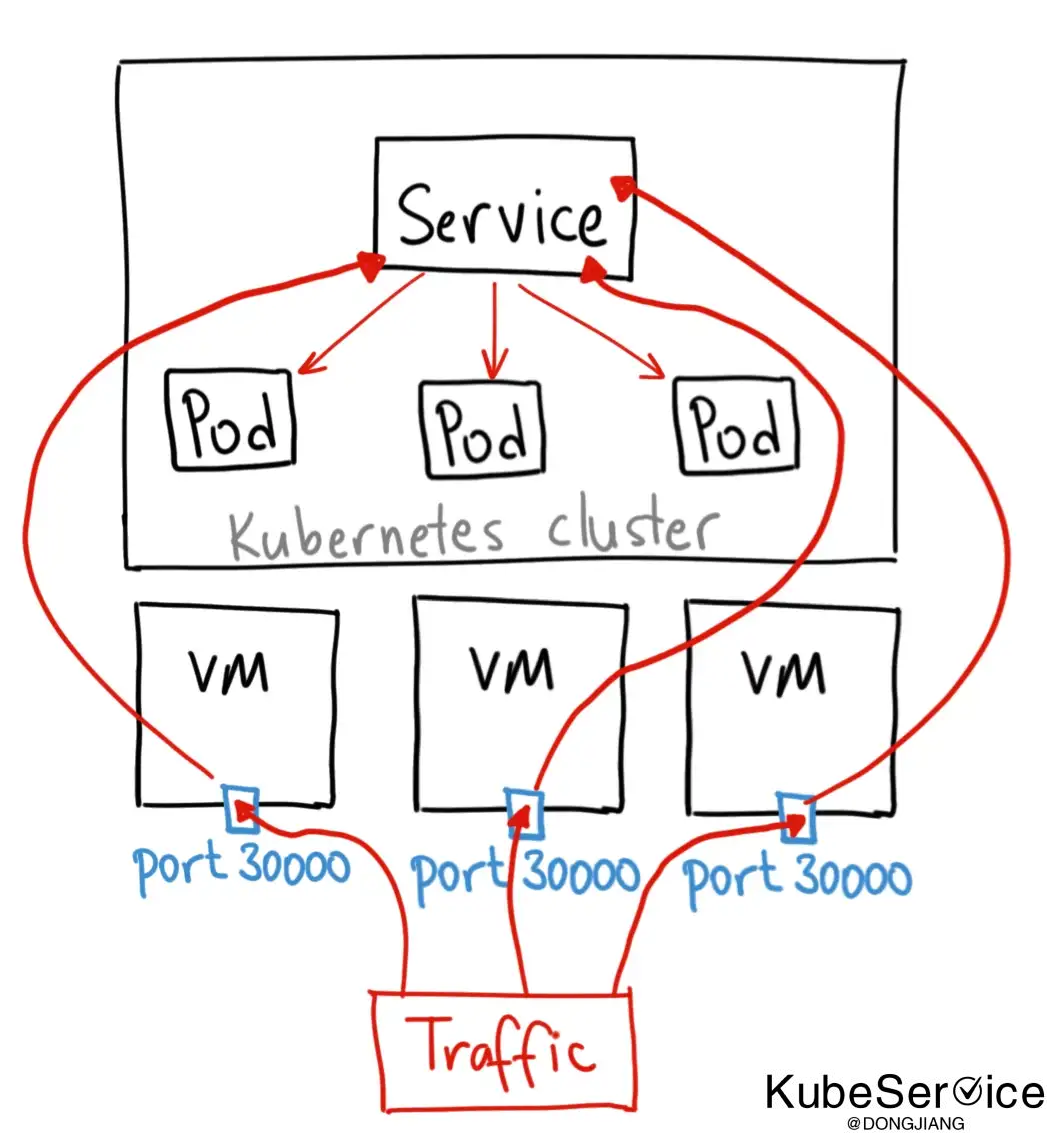
部署背景
NodePort模式的Service.yaml
apiVersion: v1
kind: Service
metadata:
name: nginx-ingress
spec:
type: NodePort
ports:
- port: 80
targetPort: 80
protocol: TCP
name: http
selector:
app: nginx-test
nginx deployment yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-deployment
spec:
selector:
matchLabels:
app: nginx-test
replicas: 1
template:
metadata:
labels:
app: nginx-test
spec:
containers:
- name: nginx
image: nginx:1.14.2
ports:
- containerPort: 80
部署结果
[root@kcs-cpu-test-m-8mzmj /]# kubectl get svc -o wide
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE SELECTOR
kubernetes ClusterIP 192.168.3.1 <none> 443/TCP 88d <none>
nginx-ingress NodePort 192.168.3.159 <none> 80:30830/TCP 91m app=nginx-test
opentracing-demo ClusterIP 192.168.3.119 <none> 8080/TCP 47d app=opentracing-demo
[root@kcs-cpu-test-m-8mzmj /]# kubectl get deployment -o wide | grep "app=nginx-test"
nginx-deployment 5/5 5 5 85m nginx nginx:1.14.2 app=nginx-test
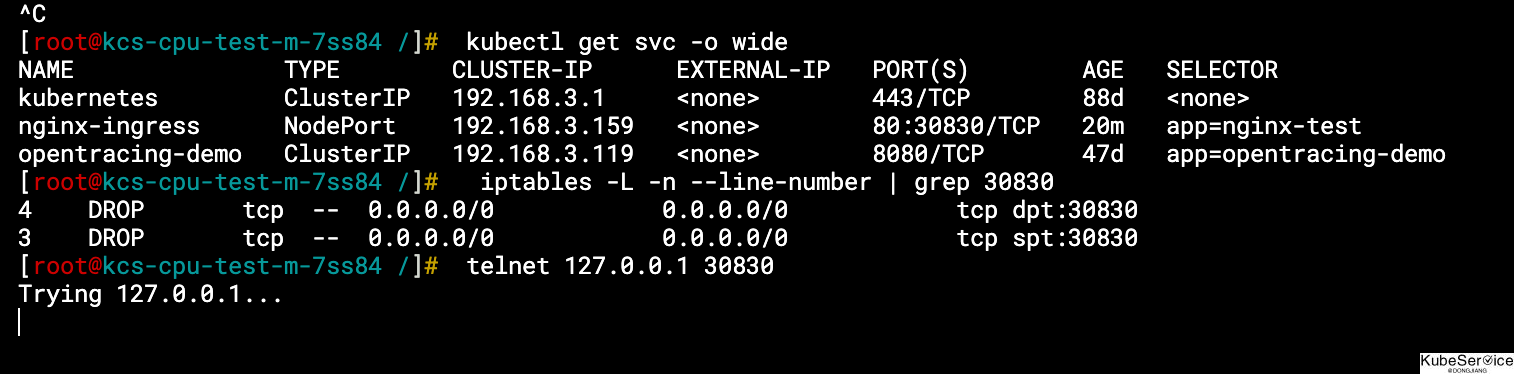
iptables 封禁方式
封禁方式:
iptables -A INPUT -p tcp --dport 30830 -j DROP
iptables -A OUTPUT -p tcp --sport 30830 -j DROP
结果:
「如果这篇文章对你有用,请随意打赏」
FEATURED TAGS
agent
apiserver
application
bandwidth-limit
cgo
cgroupfs
ci/cd
client-go
cloudnative
cncf
cni
community
container
container-network-interface
containerd
controller
coredns
crd
cuda
custom-controller
deployment
device-plugin
docker
docker-build
docker-image
drop
ebpf
ecology
egress
etcd
gitee
github
gitlab
golang
governance
gpu
gpu-device
hpa
http2
image
ingress
iptables
jobs
kata
kata-runtime
kernel
kind
kubelet
kubenetes
kubernetes
library
linux-os
logging
loki
metrics
monitor
namespace
network
network-troubleshooting
node
nodeport
nvidai
ollama
operator
pingmesh
pod
prestop
prometheus
proxyless
pvc
rollingupdate
schedule
scheduler
serverless
sglang
sidecar
sigtrem
systemd
tensorrt-llm
throttling
timeout
tools
traceroute
vllm
